EDR/EPP Fails to Protect Your Browser— Why?
By Rick Deacon on February 24, 2021
CrowdStrike, Carbon Black, and other EDR solutions can’t access browser information, preventing them from stopping modern attacks or providing any visibility.
Source: Google Chromium Blog
Modern browsers prevent problems that propagate from the browser to the OS, by encrypting data and memory. By doing so, EPP and EDR tools can’t retrieve or write data directly to the browser without a third-party. That means there’s a gap in your endpoint protection, which just so happens to be where most people are working, the browser.
By leaving the browser vulnerable, you’re leaving your endpoint devices open to spearphishing, malicious downloads, extension data leaks, malvertising, and there’s no visibility into any of it.
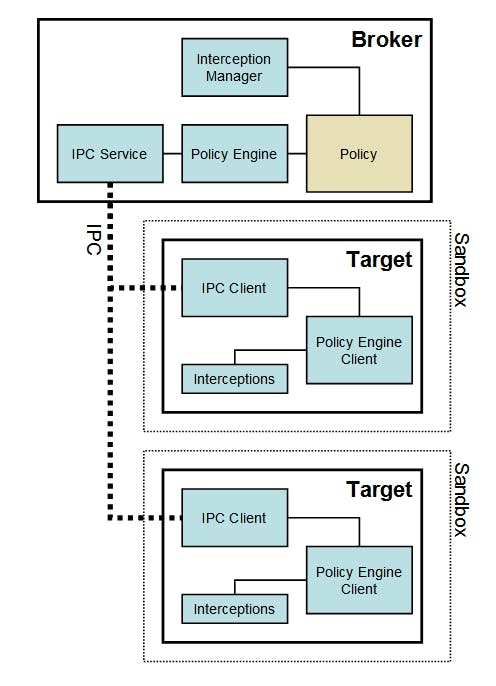
What is browser sandboxing?
Sandboxing occurs at three layers: Side-Channel Sandbox, Code Execution Sandbox, HTML Sandbox.
The sandbox is a C++ library that allows the creation of sandboxed processes — processes that execute within a very restrictive environment. The only resources sandboxed processes can freely use are CPU cycles and memory. For example, sandboxes processes cannot write to disk or display their own windows. What exactly they can do is controlled by an explicit policy. Chromium renderers are sandboxed processes.
An extension of browser security is the sandboxing of memory and storage from side-channel attacks (ex: installers that would install browser extensions bundled with other software). That sandbox uses an encrypted SQLite database to store browser history and OS default protected memory from external processes scanning memory (if available by hardware/OS).
What does and doesn’t it protect against?
The sandbox stops malicious code running inside the sandbox. Such code cannot install persistent malware in the user‘s account (because writing to the filesystem is banned). Such bugs also cannot read and steal arbitrary files from the user’s machine.
In Chromium, the renderer processes are sandboxed and have this protection. After the NPAPI removal, all remaining plugins are also sandboxed.
The sandbox does not stop bugs in system components such as the kernel it is running on.
The gap in EDR/EPP software
If you’re not familiar, Endpoint Protection Platforms(EPP) and Endpoint Detection and Response platforms(EDR) offer a method of protection and data collection for devices.
The main features of an EDR are:
- Stopping malicious activity
- Incident data search and investigation
- Suspicious activity detection
- Suspicious activity validation
- Data exploration
EDR/EPP solutions are put in place to protect the endpoint entirely but there’s no mitigation for any browser based risk. This leaves a gaping hole in company’s endpoint security goals.
Browser based attacks that go unchecked include:
- Malicious software
- Malicious browser extensions or data leakage
- Phishing, spearphishing, and malvertising
- Social engineering attacks
- Suspicious browsing activity
Furthermore, there’s no method of collecting any data around an incident or potentially hazardous activity.
How do you fill the gap?
In order to properly protect the browser and complete your endpoint protection plan, you need a Browser-EDR(B-EDR) to provide protection and visibility.
A B-EDR instantly fills the gap left by your EDR with:
- Native Browser Isolation
- Incident data collection with pre-encrypted traffic analysis
- Spearphishing & malware download protection
- Malvertising safeguards & centrally managed adblock
- Browser extension auditing, blocking, and risk information
- Data loss prevention and investigation
Airlock is the world’s first B-EDR.
Airlock deploys in under 60 seconds, reduces risk across all browsing, provides data that is typically unreachable, and increases your endpoint protection effectiveness.
Airlock itself also uses sandboxing. The Native Browser Isolation sandbox is implemented via HTML Sandboxing. This method of sandboxing prevents end users from entering credentials, downloading files, or allowing malicious scripts on dangerous websites.
Try Airlock now, instantly, at https://www.apozy.com.
Conclusions
Protecting your endpoints is critical in any modern security stack. In order to prevent breaches and lateral movement, endpoints must be completely protected. To achieve the goal of layered security, browser protection and visibility must be considered as a standard.
About Apozy
Founded in April of 2014 in San Francisco, we are a venture-backed motley crew of passionate hackers building cybersecurity technologies to make the world's information faster, cleaner and safer to access.

