What is Browser Endpoint Detection and Response?
By Rick Deacon on October 15, 2020
Savvy security folks are aware that determined threat actors and spearphishers can be patient and resourceful in their efforts to breach your organization and defeat your defenses. In the past few years, attacks have moved to the most vulnerable piece of your network - your browser. Email, operating systems, and endpoint software is patched and kept secure while attackers deliver social engineering attacks completely unhindered.
This failure is often a lack of visibility and little to no protection from malicious websites. Browser Endpoint Detection and Response (B-EDR) is the solution for addressing this challenge. This article offers insight into what B-EDR is, how it works, and why it is a key component of endpoint security.
What is Browser Endpoint Detection and Response?
B-EDR has one of the most critical security capabilities there is: visibility. Visibility into browsers is traditionally limited, with encryption and browser to OS sandboxes keeping access to data and activity limited.
To define B-EDR more simply, it records browser activities and events taking place on endpoints and provides security teams with the visibility they need to uncover incidents that would otherwise remain invisible.
This article is will give you a better understanding of browser endpoint detection and response by explaining where it fits in a security strategy. By the end, you’ll know the benefits of incorporating B-EDR into your security approach.
Expert Tip
What is the difference between B-EDR and a secure web gateway(SWG)? SWGs is the prevention component of endpoint security, which aims to stop threats from entering the browser. When threats slip past an SWG, B-EDR detects that activity and automatically stops the threat before it causes any damage.
B-EDR Security Capabilities
According to Gartner, effective endpoint detection and response must include the following capabilities:
- Incident data search and investigation
- Alert triage or suspicious activity validation
- Suspicious activity detection
- Threat hunting or data exploration
- Stopping malicious activity
What Does B-EDR Do?
Here are the six key aspects of B-EDR you should know and understand:
1. Visibility:
Real-time visibility across all your browsers allows you to view malicious activity, even as attacks attempt to breach your environment, and stop them immediately.
2. Threat Database:
Effective B-EDR requires massive amounts of telemetry and traffic collected from browsers. Data is enriched with context so it can be mined for signs of attack with a variety of analytic techniques, including Visual AI.
3. Real-Time Protection:
Relying solely on scanning services or threat intel leads to the “silent failure” that allows data breaches to occur. Effective B-EDR requires approaches that determine indicators of imposter sites, so you are alerted of suspicious activities at time of click.
4. Insight and Intelligence:
A B-EDR solution that integrates user, browser, extension, and traffic data can provide context, including details on the type of social engineering and information about the attack.
5. Fast Response:
B-EDR that enables an automatic response to incidents can stop an attack before it becomes a breach and allows your users to get back to work immediately.
6. No Endpoint Impact:
Having a browser extension based B-EDR solution is the only way to ensure zero impact on endpoints, while making ensuring that data is collected unencrypted and attacks are stopped in real-time. Cloud management of the B-EDR is also critical to ensure deployment and management is simple.
Learn More
Watch our on-demand webcast to see the role of Native Browser Isolation in the context of B-EDR.
Airlock B-EDR
The Airlock B-EDR provides next-gen capabilities that surpass conventional defenses, which leave you open to failure and can allow attackers to deliver spearphishing undetected. The solution lies in having continuous and comprehensive real-time protection and visibility into what is happening within your browsers. Airlock also delivers the ability to apply behavioral analysis and actionable intelligence to stop an incident from turning into a breach.
Apozy B-EDR provides the following critical capabilities:
Automatically Detects & Respond to Targeted Attacks
Airlock pairs comprehensive visibility across browsers with Visual AI that analyzes billions of sites in real time to automatically detect suspicious pages. After detection, sites are sandboxed at time of click.
Understanding the visual branding of sites as part of a broader picture allows Airlock to apply security logic from Visual Artificial Intelligence. If a visited site matches a known brand, the Airlock extension will identify the activity as malicious and automatically sandbox the malicious page using Native Browser Isolation.
Time of Click Native Threat Sandboxing
Airlock isolates next-gen threats on the web via Native Browser Isolation. It allows organizations to remain safe while the browser automatically takes swift and instantaneous action by neutering potentially hazardous pages.
When a page is sandboxed, it can still be viewed and explored, but it will remain contained unless it is unlocked by a user or administrator.
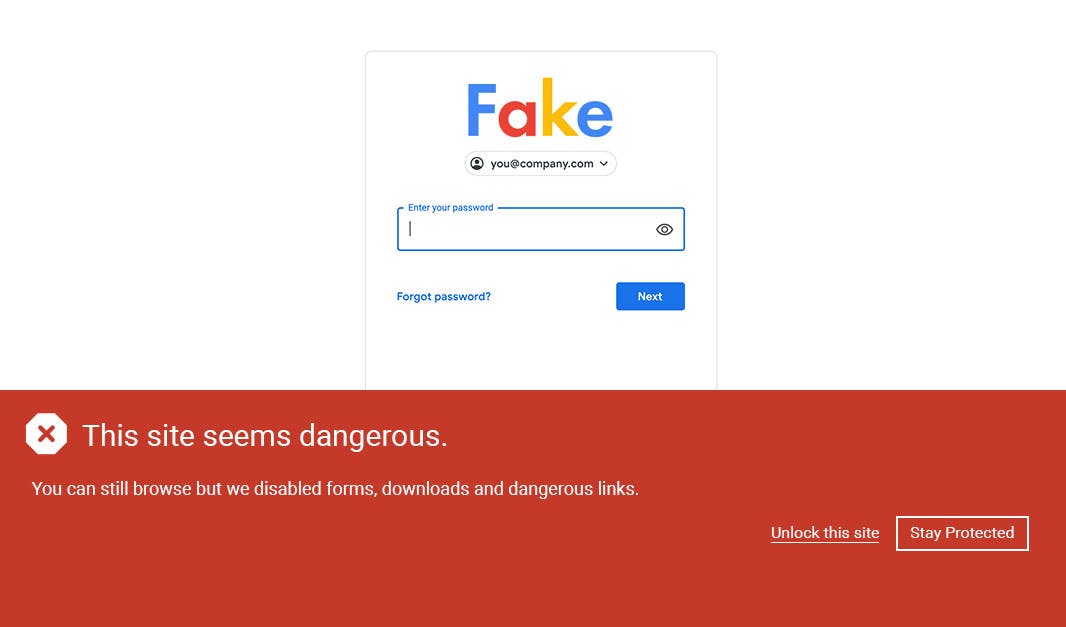
When it comes to responding to emerging threats, time is of the essence and responders need visibility in depth and in real time, so they can remediate with speed and decisiveness. Airlock reports sandboxed sites in real-time, providing the enhanced visibility that enables security teams to immediately understand the threats they are dealing with, while creating zero impact on performance.
Provides Real-Time and Historical Visibility
Airlock acts like a DVR in the browser, recording browsing activity to monitor and report incidents. Browsing activity is recorded pre-encrypted, much like SSL inspection, but without the use of a proxy or gateway. Customers are given comprehensive visibility into everything that is happening on their endpoints’ browsers from a security perspective. Airlock tracks browsing data, extensions, and ads that are blocked.
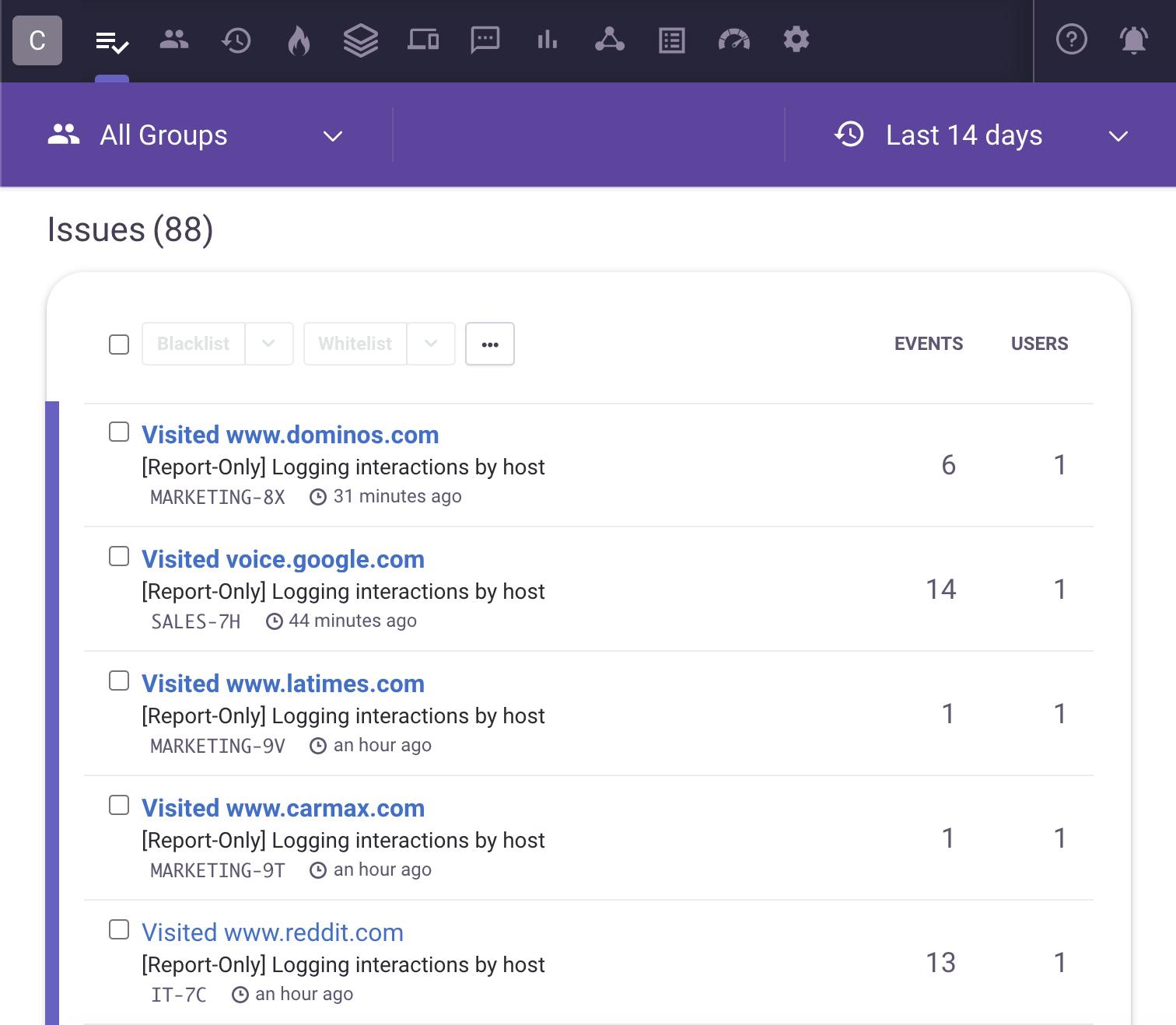
This gives security teams the useful information they need, including:
- Browsing data, with full URLs unencrypted.
- Side-loaded and third party requests.
- Uploads and downloads with destination and source.
- Browser extensions that leak private information from your browser.
- Ads that contain potential malvertising.
- Context with user, device information, and timestamps.
- Incident reporting and timelines.
This complete oversight of security-related browser activity allows security teams to “shoulder surf” on malicious activity in real time.
Manage and Block Browser Threats Beyond Phishing
Airlock reports on threats that go unseen. Browser extensions frequently have access to most everything on your screen and may report whatever it contains to a cloud service. Often times, these same extensions have no privacy policy, providing no visibility on where your data is going or who owns it. By delivering complete visibility into browser extensions that may be leaking private information, Airlock allows security teams to block malicious software with one click before it causes damage.
Malvertising attacks contain phishing that target your organization and bypass 99% of security tools, because they’re embedded in existing, trusted ad networks. These ad networks flood information to your search results and apps you use everyday. The only way to stop malvertising is to use ad block. Airlock is the first of its kind, a centrally managed ad block that is configured from the cloud management console. Instantly apply blocking rules to groups based on risk profiles.
Complete Platform
With Airlock’s cloud-native architecture, lightweight browser extension and unified console, response capabilities can be delivered to any system anywhere in the world with zero impact on cost or performance.
B-EDR should be a part of your endpoint security strategy, here’s why:
Reason #1: Prevention alone can’t ensure 100 percent protection
When prevention fails, your organization can be left hanging by its current phishing solutions. Attackers take advantage of this situation to attack the low hanging fruit, your browser.
Reason #2: Organizations lack the visibility needed to effectively monitor browsers
When a breach is finally discovered, the victim organization can spend months trying to remediate the incident because it lacks the visibility required to see and understand exactly what happened, how it happened and how to fix it — only to see the attacker return within a matter of days.
Reason #3: Artificial intelligence is needed to stop a breach
Organizations may not only lack the visibility required to understand what is happening in browsers, it may not be able to stop an attack as it occurs.
Reason #4: Having the data is only part of the solution
Even when data is available, security teams need the resources required to analyze and take full advantage of it. This is why many security teams find that soon after they’ve deployed an event collection product, such as a SIEM, they are often facing a complex data problem. Challenges around knowing what to look for begin cropping up and other problems surface before their primary objectives can even be addressed.
Reason #5: Remediation can be protracted and costly
Without the capabilities listed above, organizations can spend weeks trying to discern what actions to take — often the only recourse is to reimage machines, which can disrupt business processes, degrade productivity and ultimately cause serious financial loss.
About Apozy
Founded in April of 2014 in San Francisco, we are a venture-backed motley crew of passionate hackers building cybersecurity technologies to make the world's information faster, cleaner and safer to access.


